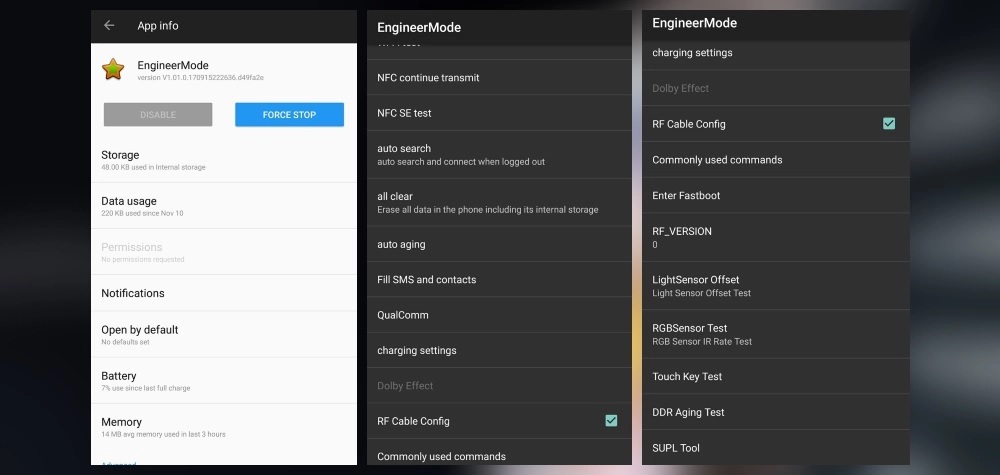
There has been a lot of discussions on the amount of data transmitted by Oneplus devices to the mother ship. A security researcher suing the monikor Elliot Alderson decided to dig deeper to find out what data was being sent. As he dug through the OS (OxygenOS) on his phone he discovered an EngineerMode app. This app (assumed to be an internal testing tool for QA) gives access to all aspects of the phone, including rooting. A quick check for Oneplus owners it to enter *#808# SSID, which will bring up the app if present. A hcak (for now) requires physical access.
Author: Kristian
Apple’s next exclusive TV content
Apple’s plans to enter the consumer media market have been know for long, and now more confirmed deals are public. The deal with Steven Spielberg on the resurrection of the Amazing Stories anthology has already been announced, now Apple has signed the right for 2 seasons of TV based on the Brian Stelter’s book ‘Top of the Morning: Inside the Cutthroat World of Morning TV “ and will star Jennifer Aniston and Reese Witherspoon.
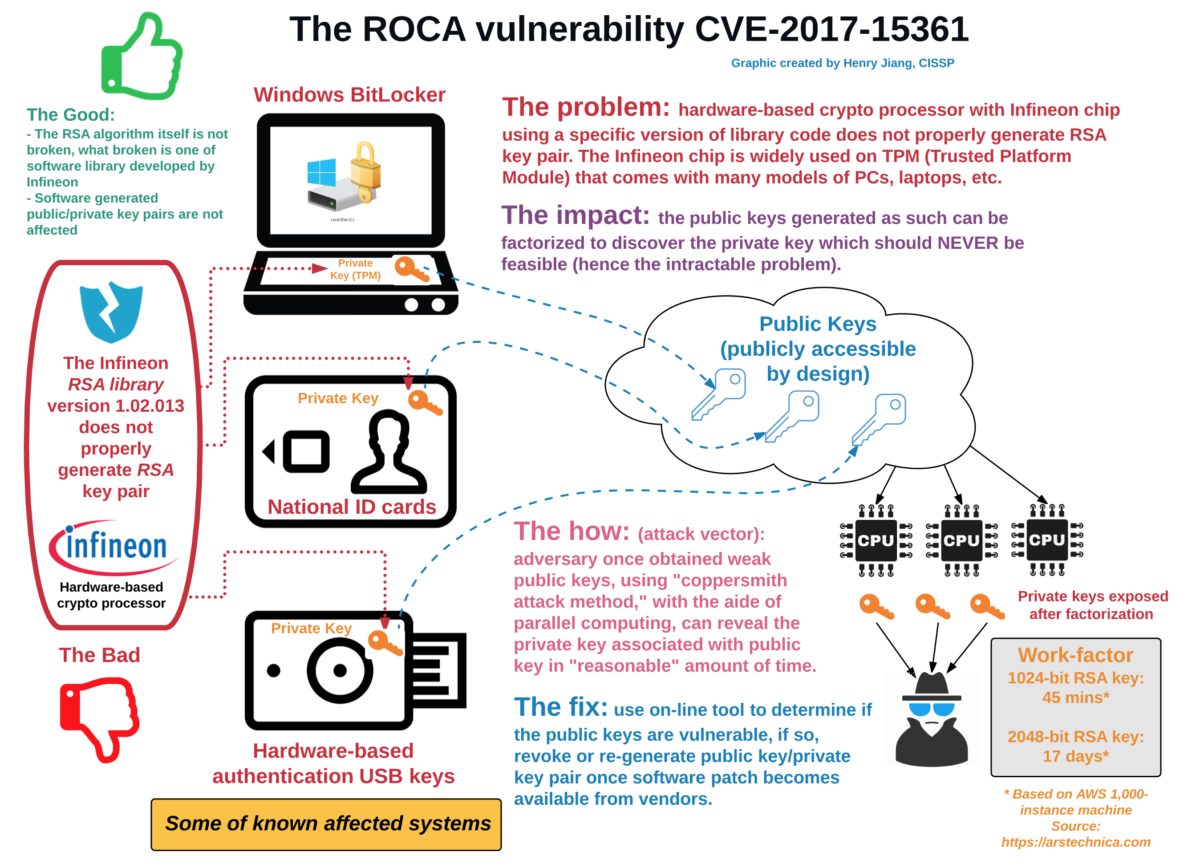
The Return of Coppersmith’s Attack
The Infineon-developed RSA Library version v1.02.013, arguably one the most commonly used libraries for RSA Prime Calculations in almost all major public PKI solutions has been discovered to contain a major flaw in the way the randomness of the keys are calculated. A study by Matus Nemec, Marek Sys, Petr Svenda, Dusan Klinec and Vashek Matyas shows that “…our discovery of an algorithmic aw in the construction of primes for RSA key generation in a widely-used library of a major manufacturer of cryptographic hardware. The primes generated by the library suffer from a signicant loss of entropy”.
This has had massive impacts, perhaps the most public is the cancellation of a major part of the current generation of National ID Cards in Lithuania. Remember that security without randomness is no security!
Facebook’s shadow profiles
Facbook’s People You May Know algorithm has been of interest for security minded people for a while. A number of “weird” and inappropriate suggestions has led to Gizmodo digging deeper into the underlying systems and approaches. In fairness, most of the approach is clearly highlighted in the respective EULA’s, but how many users actually reads them?
Another Crypto Currency Hard Fork?
Etherum (the most referred to competitor to Bitcoin currently) has had another “incident”. You may remember the USD 32 million USD hack on Etherum in July and the subsequent (heavily criticized) hard fork to zero out the hack. Now a “mistake” from a developer has locked down wallets worth USD 300 million. The attack relates to a quirk in Etherum’s multisignature wallets, and will most likely require another hard fork to rectify. Again a warning that crypto currencies are still evolving, in most cases at a slower pace than the money thrown at it.
KRACK: Key Reinstallation Attacks
Mathy Vanhoef and Frank Piessens of KU Leuve have discovered a critical flaw in the way WPA2 encryption for all known WiFi implementations. Some time to caveat on the width of the discovery, the attacker needs physical access to the network, and will only see non-encrypted transmissions. Until the vendors patch their implementations the only interim solution is to treat your home WiFi as you would a public WiFi, using HTTPS and in an ideal world VPN form the individual client.
This overview on Github shows the current state of fixes from the vendors. I somewhat sadly note that the majority of my HW is under the “No Known Official Response” category!
ATM Hacking, summary of the latest techniques
Trend Micro has put up an report on the latest techniques used to hack ATM’s with a focus on the recent emergence of purpose written malware and their impacts. A good read!
Sports Hacking
This is (I suppose) an logical evolution of technology and its use: The Boston Redsox have been caught using Apple Watches to steal New York Yankees pitching calls. For those that don’t follow baseball, the pitcher and the catcher will through hand signals agree on the required pitch. The Red Sox relayed this info to the batting coach, and the batter was informed the most likely pitch to come.
An informed write-up can be found on NY Times.
More Bluetooth Issues in the Wild
Bluetooth seems to be the flavour of the month lately in hacking, and a number of issues have been highlighted lately. The “best” on so far is the blueborne – an airborne hack through Bluetooth with great potential for harm. An analysis from Armis shows how it works.
When should you stop trusting you vendors?
There has always been an uncomfortable relationship between a customer and their security vendors, in particular with the relationship between the vendor and state agencies. Normally a concern with US vendors, bur lately Kapersky has been accused of providing Russian Agencies access to their customers. It should be pointed out that the proof provided is not good, but enough for actors like the US Government banning the use of all Kapersky products. An breakdown of the allegation can be found in this analysis from ArsTechnica, summing up the info from primarily sources behind pay-walls.