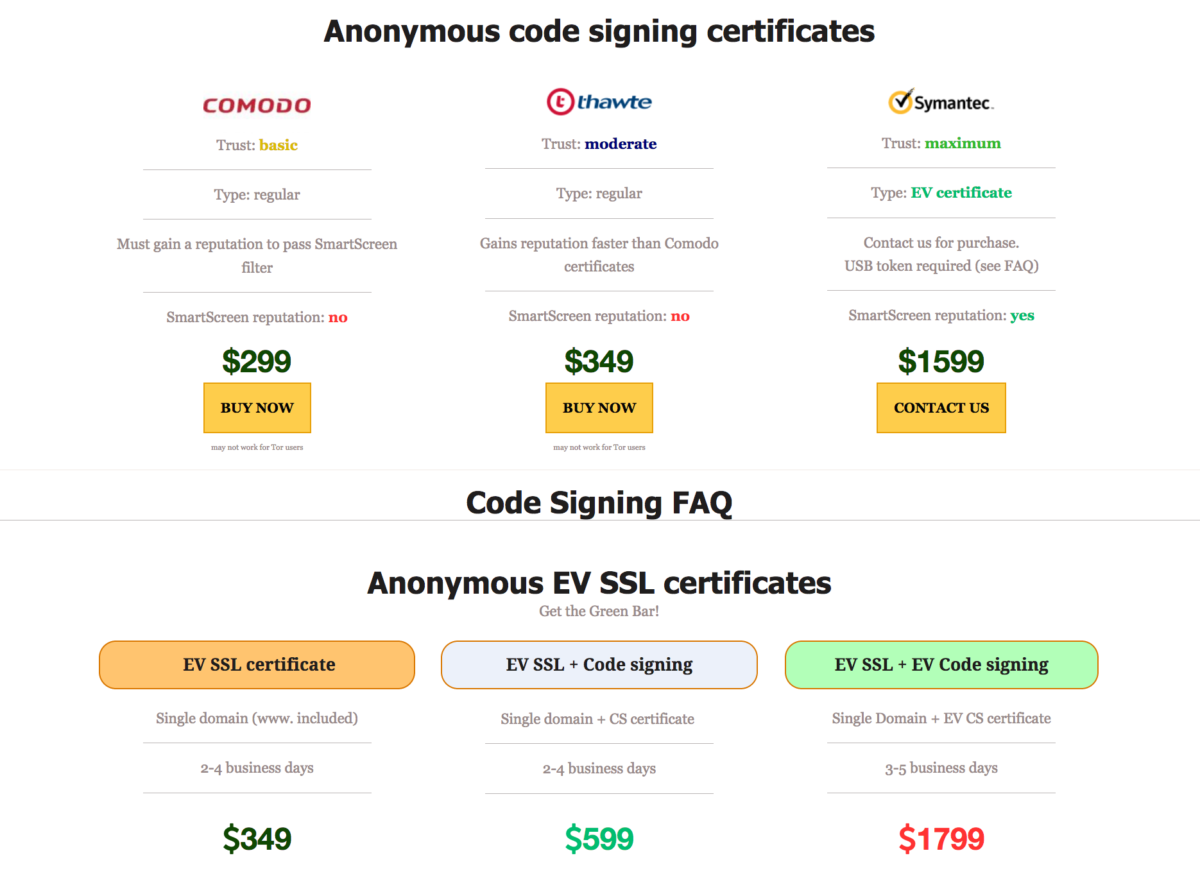
The previous trend of using stolen certificates to digitally sign malware (to circumvent OS’s requirements for valid digital signatures om files to install SW) has been overtaken by black hats issuing counterfeit certificates pretending to be the institution the certificates are issued to. Social engineering to the next leve is one way of looking at this. Recorded Future has an analysis of the current market place, with a tracking of the 3 largest dark web merchants and their volumes over the last 5 years. Also a breakdown of the current offerings available. Note that the high-end certs are Symantec Certs, the CA that got phased ut by the browser vendors after numerous issues, so the hope is that this will remove the EV certificates from this kind of use.
Author: Kristian
[Updated] More Apple iOS source code leaks (iBoot)
Yet more Apple source code has been leaked, this time around the iBoot elements of IOS. Although from an older build of IOS (9x) it should be close to the current implementation. Initially leaked on Reddit by a user named apple_internals and subsequently removed, now posted in Github for maximum availability. An good article on Motherboard does some initial analysis and impact analysis. It’s a shame jailbreaking has gone out of Vogue, this will make it a lot simpler to do.
[Update] Apple has released the following statement” Old source code from three years ago appears to have been leaked, but by design the security of our products doesn’t depend on the secrecy of our source code. There are many layers of hardware and software protections built in to our products, and we always encourage customers to update to the newest software releases to benefit from the latest protections.”
A DMCA notice has been sent to Github to take down the source code.
The real background story on the Russian hacking of the White House and the Democratic Party
Dutch Newspaper De Volkskrant has published the story of how the Dutch Intelligence Services (AIVD) hacked the infamous Russian hacking group Cosybear / APT29 and monitored how they hacked into the US and how this was fought withe the Americans. Also on the aftermath of these findings being made public by the Trump Administration. Another country now deeply skeptical to sharing Intel with the US along the previous leaks made this year.
[Update] More info can be found at Nieuwsuur.
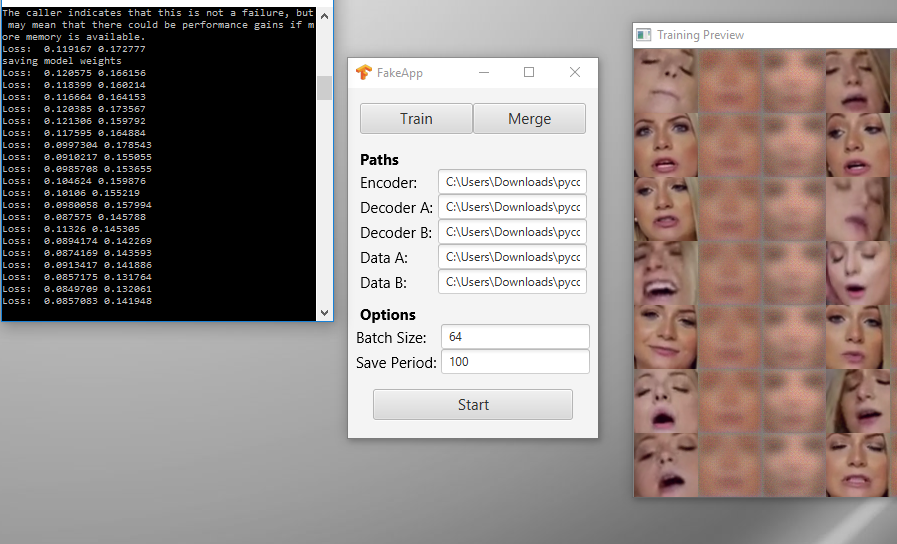
Machine Learning gone bad
I suppose every new technology will eventually be misused, and this has now come to machine learning and facial recognition algorithms. As reported by Motherboard an app has been launched on reddit using NVIDA’s CUDA framework to morph faces onto another body, to create realistic videos as an outcome. Of course (in an forum dominated by teenage boys) the initial activity is to use celebrity faces in porn scenes, but it raises another worry about trusting digital images and video files in a wider use of this technology.
How much can a Malware payload actually do?
Kapersky has released an advisory on Securelist on a new major Android Malware, originating (it seems) from Italy. Skygofree (as it has been named) goes above and beyond what has been seen before. Skygofree is capable of taking pictures, capturing video, and seizing call records, text messages, gelocation data, calendar events, and business-related information stored in device memory. Skygofree also includes the ability to automatically record conversations and noise when an infected device enters a location specified by the person operating the malware. Also a clever use of Androids Accessibility Service gives backdoor access to Whatsapp. Deeper analysis leads to finding a set of windows components indicating an almost full Windows implementation of the above.
For those looking to validate if they are impacted, here are the indicators.
Uber/Waymo: Jacob’s letter released to the public
The letter written by Richard Jacobs to senior management in Uber (leading to his job demotion and eventually leaving Uber) that delayed the current court case between Waymo (Google) and Uber when discovered. This document has now been (mostly) made public by the court. The complete document can be found on Scripted, some initial analysis can be found on Engadet, CNN and on Verge.
This gives an uncensored and scary insight of how corporate espionage and hacking seems the be a key part of Ubers business model and operations.
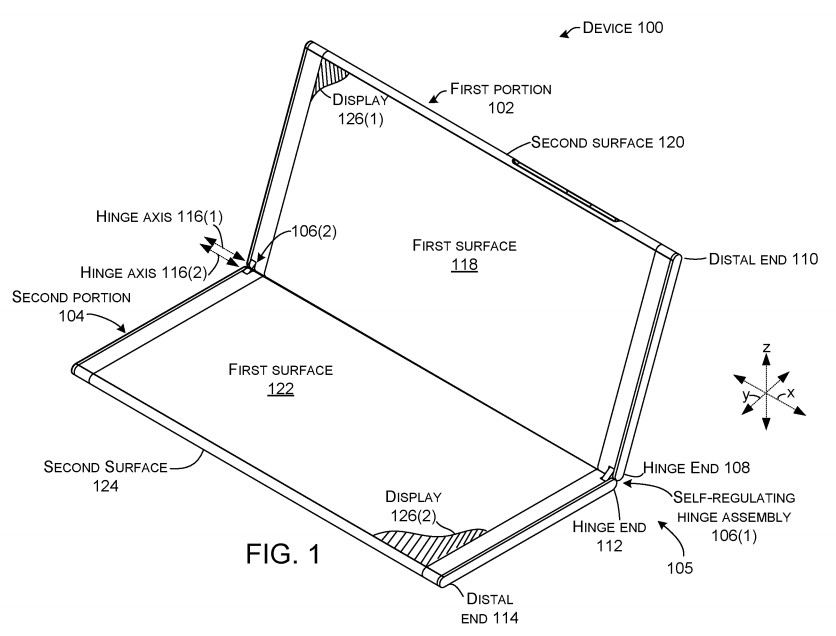
Further Microsoft Patents: Is the Windows Phone back on?
I have mentioned a couple of times that keeping an eye on patent applications filed by Microsoft can give you a glimpse of things to come. Much like the surface book series was preempted by the key technologies patented, there is now more patent applications for the much debated Microsoft mobile terminal (sometimes referred to by the internal (?) project name Courier). A good summery in Arsthecnica, showing more and more of the expected device.
A true physical “man in the middle” attack
There has been known weaknesses with the various key less entry solutions among cat manufacturers, the debacle on the system used by JEEP springs to mind. Now we see a weakness in the Mercedes Benz solution. In a video released by the West Midlands Police in the UK we see thieves sniffing out the key code from the key inside of the house, and then transfers it to a sender by the car to open and start the car. Time to look at at NFC blocking key storage I suppose.
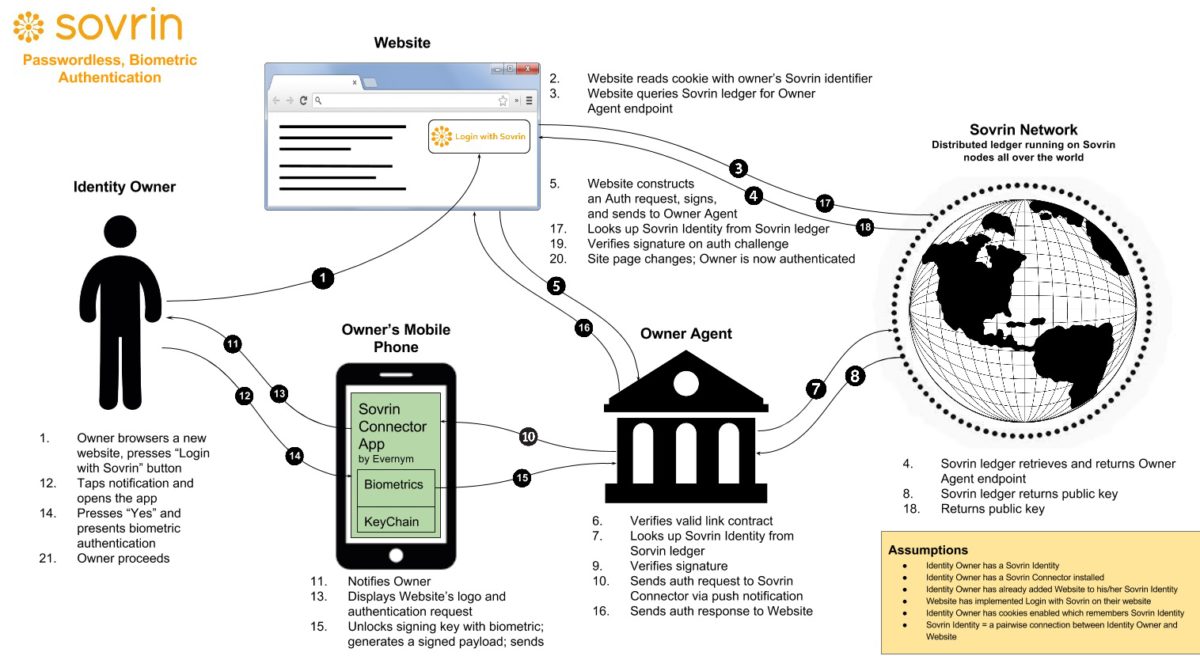
Digital Identities – an distributed approach
Traditional Digital identity schemes, such as the X509 certificate approach and similar, has always carried substantial overhead and cost to reach non-repudiation. With the explosion of distributed ledgers in areas such as digital currencies and the current reluctance by consumers on using IOT solutions due to privacy and security issues there is a need for an alternative. The Sovrin foundation has taken this and have made an “Self-Sovereign” Identity solution. Based on open-source distributed ledger technology this approach has a lot of potential, in particular in the theoretical ability to self manage devices and their trust relationships. The illustration here shows how this works in the real world.
Mass Surveillance is alive and kicking
Amazon S3 buckets belonging to American inteligense have been found open to the public by researchers from the Upguard Cyber Risk Team. 3 buckets, “centcom-backup,” “centcom-archive,” and “pacom-archive” (Centcom = American Military Central Command, Pacom = American Pacific command) represents 8 years of Social Media scraping with up to 1.8 Billion posts collected. Posts, users, IP numbers, password hashes etc all collected. Clues left leads to some information on the vendors involved and the tools used to analyze the data. Remember: nothing is private on Internet!

![[Updated] More Apple iOS source code leaks (iBoot)](https://www.solberg.co.uk/wp-content/uploads/2018/02/1518047804451-Screen-Shot-2018-02-07-at-63528-PM.jpg)