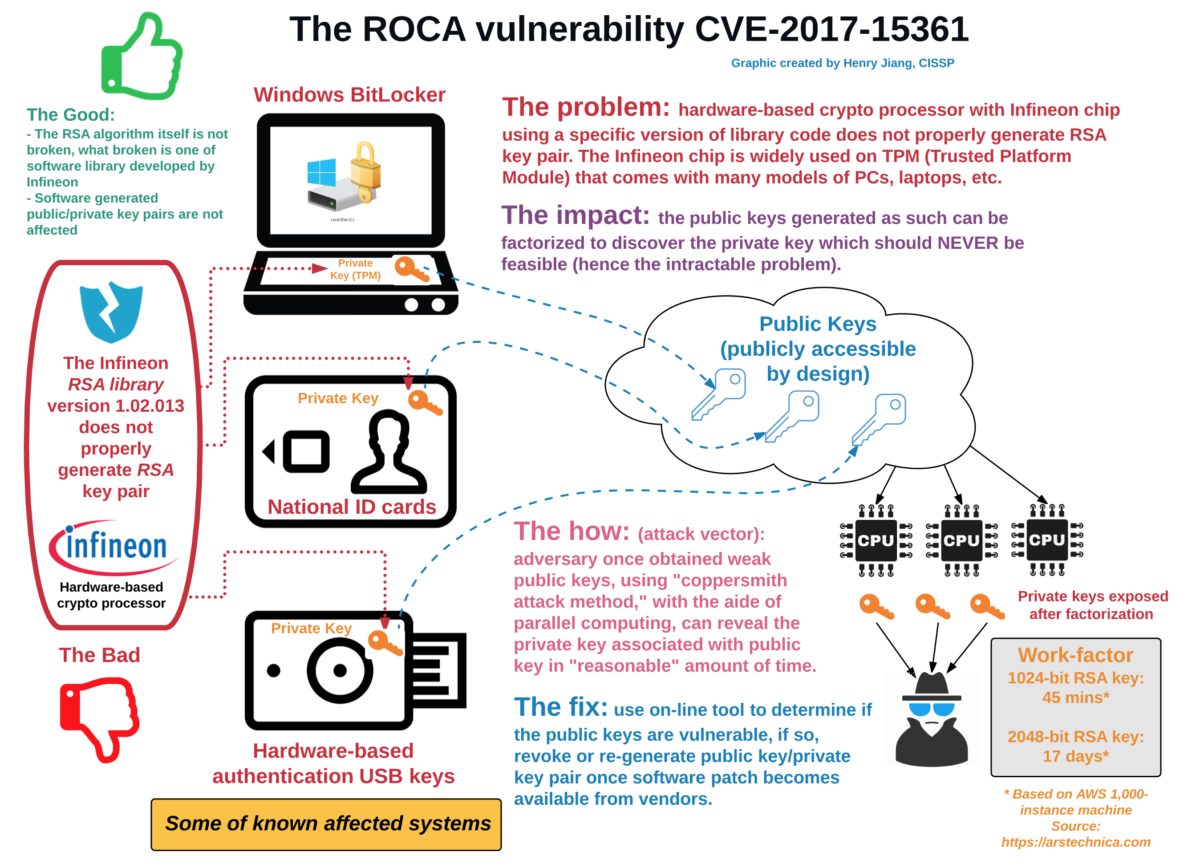
The Infineon-developed RSA Library version v1.02.013, arguably one the most commonly used libraries for RSA Prime Calculations in almost all major public PKI solutions has been discovered to contain a major flaw in the way the randomness of the keys are calculated. A study by Matus Nemec, Marek Sys, Petr Svenda, Dusan Klinec and Vashek Matyas shows that “…our discovery of an algorithmic aw in the construction of primes for RSA key generation in a widely-used library of a major manufacturer of cryptographic hardware. The primes generated by the library suffer from a signicant loss of entropy”.
This has had massive impacts, perhaps the most public is the cancellation of a major part of the current generation of National ID Cards in Lithuania. Remember that security without randomness is no security!
Day: November 8, 2017
Facebook’s shadow profiles
Facbook’s People You May Know algorithm has been of interest for security minded people for a while. A number of “weird” and inappropriate suggestions has led to Gizmodo digging deeper into the underlying systems and approaches. In fairness, most of the approach is clearly highlighted in the respective EULA’s, but how many users actually reads them?
Another Crypto Currency Hard Fork?
Etherum (the most referred to competitor to Bitcoin currently) has had another “incident”. You may remember the USD 32 million USD hack on Etherum in July and the subsequent (heavily criticized) hard fork to zero out the hack. Now a “mistake” from a developer has locked down wallets worth USD 300 million. The attack relates to a quirk in Etherum’s multisignature wallets, and will most likely require another hard fork to rectify. Again a warning that crypto currencies are still evolving, in most cases at a slower pace than the money thrown at it.